Windows Exploit Development – Part 6: SEH Exploits
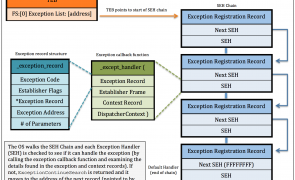
Introduction The buffer overflow exploits covered so far in this tutorial series have generally involved some form of direct EIP overwrite using a CALL or JMP instruction(s) to reach our shellcode. Today we’ll take a look at a different approach using Windows Structured Exception Handling (SEH). Before I begin explaining the basic mechanics of Windows Structured Exception Handling (as it’s implemented in an x86, 32-bit environment) it bears mentioning that…
Read more...Passive Reconnaissance
are closed
Introduction Recently, while watching the House Committee hearings on the security of Healthcare.gov, I was disappointed to hear testimony likening passive reconnaissance to a form of unauthorized/illegal activity that involved potentially invasive actions such as port/vulnerability scanning. To the contrary, passive recon can be one of the most useful and unobtrusive methods of data gathering for any penetration test or security assessment. In this post I outline what passive reconnaissance…
Read more...Tags:advanced search , burp , burpsuite , exploit-db , ghdb , google , google hacking , healthcare.gov , maltego , nerdydata , passive , passive recon , passive reconnaissance , pastebin , recon , reconnaissance , security , shodan
Securing Healthcare.gov – Failures, Fixes, and Next Steps
are closed

Introduction The views expressed in this blog are my own. Just to be clear, that means they are not the views of my employer, co-workers, family, friends, casual acquaintances, strangers, or anyone other than myself. There has been plenty of news coverage about the security flaws that have plagued Healthcare.gov since it went live in October 2013: Hackers: HealthCare.gov still riddled with potential security issues Exclusive: Security Risks Seen at…
Read more...Tags:Air Force , C&A , Certification and Accreditation , CMS , dave kennedy , Frank Baitman , healthcare , healthcare.gov , HHS , Kevin Charest , Larry Ponemon , Lunarline , obamacare , ponemon , security , Superior Solutions , Teresa Fryer , TrustedSec , Waylon Krush
How NOT To Restrict Cross-Domain Flash Content
are closed
Introduction Insufficient input validation is a problem I encounter practically every time I test an application. I’ve talked about relying on input validation as a prevention mechanism before (see here and item #8 here) but since it’s such a prevalent problem I figured I’d take the time to write about it once again. While a good supplemental control, by itself input validation is usually woefully inadequate. Quite frankly, it often requires much…
Read more...Tags:bounty , bug bounty , cross domain , crossdomain , flash , jpexs , paypal
Windows Exploit Development – Part 5: Locating Shellcode With Egghunting
are closed
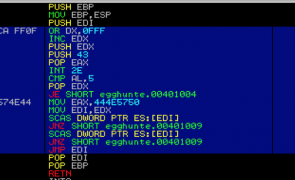
Overview In Part 4 we looked at how to find and execute your shellcode using various jump methods. In Part 5 we’re going to look at another method to find your shellcode called Egghunting. This method is especially useful when you’re faced with a small, reachable buffer (in which you can execute code) but the placement of your larger shellcode in memory is unpredictable. This post will get into quite…
Read more...Tags:coolplayer , egg sandwich , egghunter , egghunting , exploit , exploit development , omelette , shellcode , windows
Windows Exploit Development – Part 4: Locating Shellcode With Jumps
are closed
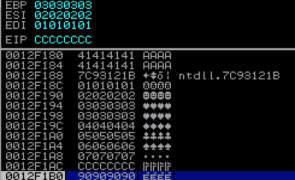
Overview In Parts 2 and 3, we built and improved upon an exploit for ASX To MP3 converter. Even though it had it’s flaws, as far as exploits go, it was pretty straightforward — direct EIP overwrite with a jump directly to a register that pointed to our shellcode. Things aren’t always that easy. Quite often you have to do a bit more work to get the application to execute…
Read more...Windows Exploit Development – Part 3: Changing Offsets and Rebased Modules
are closed

Overview In Part 2 we constructed a basic stack based overflow exploit for ASX To MP3 Converter. As I indicated in that post, the exploit itself is far from perfect. Successful EIP overwrite is influenced by the file path of the m3u file. In addition, although application modules are preferred when selecting jump/call addresses, the application DLL we used was rebased, meaning the address to our CALL EBX instruction is…
Read more...Bug Bounty Blitz!
are closed

Introduction Over the last couple of years it seems bug bounties have gained increased attention and are being embraced by more organizations — and for good reason. For companies, it can provide a cost-effective means of obtaining professional security testing and for the security community, any form of sanctioned testing against a live/production application is a good thing :). In May of this year I decided to undertake a little…
Read more...Tags:bounties , bounty , bug bounties , bug bounty , bug bounty program , bugcrowd , bugs
Windows Exploit Development – Part 2: Intro to Stack Based Overflows
are closed
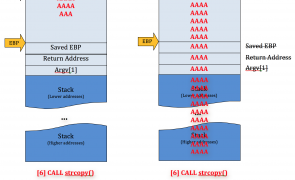
Overview Welcome to Part 2 of my Windows Exploit Development series. In the first post, I covered some basic concepts that should be considered pre-requisites for continuing with Part 2 and beyond. If you haven’t done so, I recommend at least taking a cursory look at the first post to ensure you’ve got a firm grasp on all of the concepts presented. Building on that knowledge, I now want to…
Read more...Tags:ASX To MP3 Converter , buffer overflow , debugger , exploit , immunity , mona , mona plugin , overflow , shellcode , stack based buffer overflow , stack based overflow , stack overflow
Windows Exploit Development – Part 1: The Basics
are closed
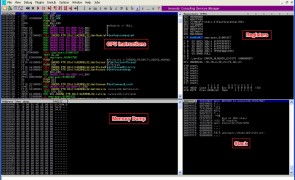
Overview Welcome to Part 1 of a series of posts on Windows Exploit Development. In this first installment I’ll cover just the basics necessary to understand the content of future posts, including some Assembly syntax, Windows memory layout, and using a debugger. This will not be a comprehensive discussion on any of these topics so if you have no exposure to Assembly or if anything is unclear after you read…
Read more... Security Sift
Security Sift
are closed